NB: THIS INFORMATION WAS SOURCED FROM ANOTHER SITE
We mentioned that Trunk Links are designed to pass frames (packets) from all VLANs, allowing us to connect multiple switches together and independently configure each port to a specific VLAN. However, we haven't explained how these packets run through the Trunk Links and network backbone, eventually finding their way to the destination port without getting mixed or lost with the rest of the packets flowing through the Trunk Links.
We mentioned that Trunk Links are designed to pass frames (packets) from all VLANs, allowing us to connect multiple switches together and independently configure each port to a specific VLAN. However, we haven't explained how these packets run through the Trunk Links and network backbone, eventually finding their way to the destination port without getting mixed or lost with the rest of the packets flowing through the Trunk Links.
This is process belongs to the world of VLAN Tagging!
VLAN Tagging
VLAN Tagging, also known as
Frame Tagging, is a method developed by Cisco to help identify packets
travelling through trunk links. When an Ethernet frame traverses a trunk
link, a special VLAN tag is added to the frame and sent across the
trunk link.
As it arrives at the end of
the trunk link the tag is removed and the frame is sent to the correct
access link port according to the switch's table, so that the receiving
end is unaware of any VLAN information.
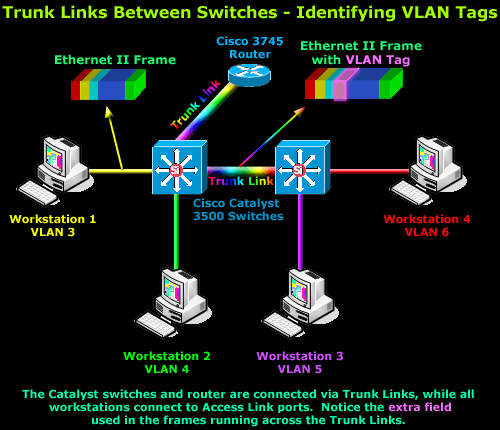
The diagram below illustrates the process described above:

Here we see two 3500 series Catalyst
switches and one Cisco 3745 router connected via the Trunk Links. The
Trunk Links allow frames from all VLANs to travel throughout the network
backbone and reach their destination regardless of the VLAN the frame
belongs to. On the other side, the workstations are connected directly
to Access Links (ports configured for one VLAN membership only), gaining
access to the resources required by VLAN's members.
Again, when we call a port 'Access Link'
or 'Trunk Link', we are describing it based on the way it has been
configured. This is because a port can be configured as an Access Link
or Trunk Link (in the case where it's 100Mbits or faster).
This is stressed because a lot of people
think that it's the other way around, meaning, a switch's uplink is
always a Trunk Link and any normal port where you would usually connect a
workstation, is an Access Link port!
VLAN Configuration, InterVLAN routing,Trunk Link
configuration for Cisco Layer 3 switches (3550, 3560 series, 3750
series, 4500 series and 6500 series switches) is covered extensively at
the following article: Basic
& Advanced Catalyst Layer 3 Switch Configuration: Creating VLANs,
InterVLAN Routing (SVI), VLAN Security – VLAN Hopping, VTP
Configuration, Trunk Links, NTP. IOS License Requirements for SVI
Routing.
VLAN Tagging Protocol
We're now familiar with the term 'Trunk
Link' and its purpose, that is, to allow frames from multiple VLANs to
run across the network backbone, finding their way to their destination.
What you might not have known though is that there is more than one
method to 'tag' these frames as they run through the Trunk Links or ...
the VLAN Highway as we like to call it.
InterSwitch Link (ISL)
ISL is a Cisco propriety protocol used
for FastEthernet and Gigabit Ethernet links only. The protocol can be
used in various equipments such as switch ports, router interfaces,
server interface cards to create a trunk to a server and much more.
You'll find more information on VLAN implementations on our last page of
the VLAN topic.
Being a propriety protocol,
ISL is available and supported naturally on Cisco products only:) You
may also be interested in knowing that ISL is what we call, an 'external
tagging process'. This means that the protocol does not alter the
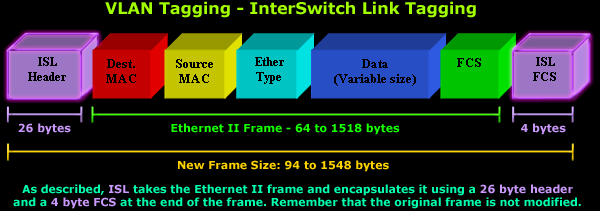
Ethernet frame as shown above in our previous diagram - placing the VLAN
Tag inside the Ethernet frame, but encapsulating the Ethernet frame
with a new 26 byte ISL header and adding an additional 4 byte frame
check sequence (FCS) field at the end of frame, as illustrated below:

Despite this extra overhead, ISL is
capable of supporting up to 1000 VLANs and does not introduce any delays
in data transfers between Trunk Links.
In the above diagram we can see an ISL
frame encapsulating an Ethernet II frame. This is the actual frame that
runs through a trunk link between two Cisco devices when configured to
use ISL as their trunk tagging protocol.
The encapsulation method mentioned above
also happens to be the reason why only ISL-aware devices are able to
read it, and because of the addition of an ISL header and FCS field, the
frame can end up being 1548 bytes long! For those who can't remember,
Ethernet's maximum frame size is 1518 bytes, making an ISL frame of 1548
bytes, what we call a 'giant' or 'jumbo' frame!
Lastly, ISL uses Per VLAN Spanning Tree
(PVST) which runs one instance of the Spanning Tree Protocol (STP) per
VLAN. This method allows us to optimise the root switch placement for
each available VLAN while supporting neat features such as VLAN load
balancing between multiple trunks.
Since the ISL's header fields are covered on a separate page, we won't provide further details here.
IEEE 802.1q
The 802.1q standard was created by the
IEEE group to address the problem breaking large networks into smaller
and manageable ones through the use of VLANs. The 802.1q standard is of
course an alternative to Cisco's ISL, and one that all vendors implement
on their network equipment to ensure compatibility and seamless
integration with the existing network infrastructure.
As with all 'open standards' the IEEE
802.1q tagging method is by far the most popular and commonly used even
in Cisco oriented network installations mainly for compatability with
other equipment and future upgrades that might tend towards different
vendors.
In addition to the compatability issue,
there are several more reasons for which most engineers prefer this
method of tagging. These include:
- Support of up to 4096 VLANs
- Insertion of a 4-byte VLAN tag with no encapsulation
- Smaller final frame sizes when compared with ISL
Amazingly enough, the 802.1q tagging
method supports a whopping 4096 VLANs (as opposed to 1000 VLANs ISL
supports), a large amount indeed which is merely impossible to deplet in
your local area network.
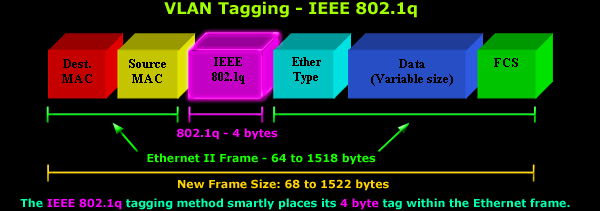
The 4-byte tag we mentioned is inserted
within the existing Ethernet frame, right after the Source MAC Address
as illustrated in the diagram below:

Because of the extra 4-byte tag, the
minimum Ethernet II frame size increases from 64 bytes to 68 bytes,
while the maximum Ethernet II frame size now becomes 1522 bytes. If you
require more information on the tag's fields, visit our protocol page
where further details are given.
As you may have already concluded
yourself, the maximum Ethernet frame is considerably smaller in size (by
26 bytes) when using the IEEE 802.1q tagging method rather than ISL.
This difference in size might also be interpreted by many that the IEEE
802.1q tagging method is much faster than ISL, but this is not true. In
fact, Cisco recommends you use ISL tagging when in a Cisco native
environment, but as outlined earlier, most network engineers and
administrators believe that the IEEE802.1q approach is much safer,
ensuring maximum compatability.
And because not everything in this world
is perfect, no matter how good the 802.1q tagging protocol might seem,
it does come with its restrictions:
- In a Cisco powered network, the switch maintains one instance of the Spanning Tree Protocol (STP) per VLAN. This means that if you have 10 VLANs in your network, there will also be 10 instances of STP running amongst the switches. In the case of non-Cisco switches, then only 1 instance of STP is maintained for all VLANs, which is certainly not something a network administrator would want.
- It is imperative that the VLAN for an IEEE 802.1q trunk is the same for both ends of the trunk link, otherwise network loops are likely to occur.
- Cisco always advises that disabling a STP instance on one 802.1q VLAN trunk without disabling it on the rest of the available VLANs, is not a good idea because network loops might be created. It's best to either disable or enable STP on all VLANs.
LAN Emulation (LANE)
LAN Emulation was introduced to solve
the need of creating VLANs over WAN links, allowing network managers to
define workgroups based on logical function, rather than physical
location. With this new technology (so to speak - it's actually been
around since 1995!), we are now able to create VLANs between remote
offices, regardless of their location and distance.
LANE is not very common and you will
most probably never see it implemented in small to mid-sized networks,
however, this is no reason to ignore it. Just keep in mind that we won't
be looking at it in much depth, but briefly covering it so we can grasp
the concept.
LANE has been supported by Cisco since
1995 and Cisco's ISO release 11.0. When implemented between two
point-to-point links, the WAN network becomes totally transparent to the
end users:

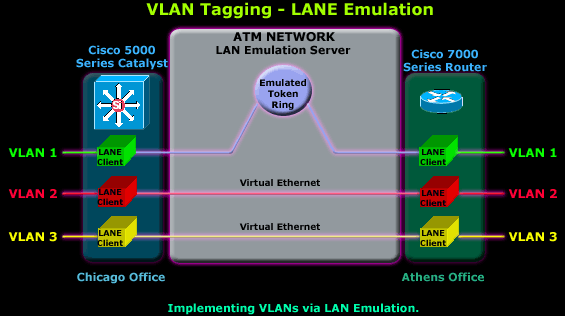
Every LAN or native ATM host, like the
switch or router shown in the diagram, connects to the ATM network via a
special software interface called 'LAN Emulation Client'. The LANE
Client works with the LAN Emulation Server (LES) to handle all messages
and packets flowing through the network, ensuring that the end clients
are not aware of the WAN network infrastructure and therefore making it
transparent.
The LANE specification defines a LAN
Emulation Configuration Server (LECS), a service running inside an ATM
switch or a physical server connected to the ATM switch, that resides
within the ATM network and allows network administrators to control
which LANs are combined to form VLANs.
The LAN Emulation Server with the help
of the LANE Client, maps MAC addresses to ATM addresses, emulating Layer
2 protocols (DataLink layer) and transporting higher layer protocols
such as TCP/IP, IPX/SPX without modification.
802.10 (FDDI)
Tagging VLAN frames on Fiber Distributed
Data Interface (FDDI) networks is quite common in large scale networks.
This implementation is usually found on Cisco's high-end switch models
such as the Catalyst 5000 series where special modules are installed
inside the switches, connecting them to an FDDI backbone. This backbone
interconnects all major network switches, providing a fully redundant
network.
The various modules available for the
Cisco Catalyst switches allow the integration of Ethernet into the FDDI
network. When intalling the appropriate switch modules and with the use
of the 802.10 SAID field, a mapping between the Ethernet VLAN and 802.10
network is created, and as such, all Ethernet VLANs are able to run
over the FDDI network.

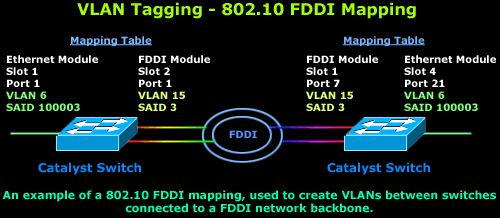
The diagram above shows two Catalyst
switches connected to a FDDI backbone. The links between the switches
and the backbone can either be Access type links (meaning one VLAN
passes through them) or Trunk links (all VLANs are able to pass through
them). At both ends, the switches have an Ethernet port belonging to
VLAN 6, and to 'connect' these ports we map each switch's Ethernet
module with its FDDI module.
Lastly, the special FDDI modules mentioned above support both single VLANs (non-trunk) and multiple VLANs (trunk).
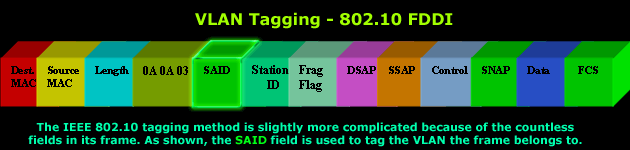
To provide further detail, the diagram
below shows the IEEE 802.10 frame, along with the SAID field in which
the VLAN ID is inserted, allowing the frame to transit trunk links as
described:

It's okay if your impressed or seem
confused with the structure of the above frame, that's normal:) You'll
be suprised to find out that the Cisco switch in the previous diagram
must process the Ethernet II frame and convert it before placing it on
the IEEE 802.10 backbone or trunk.
During this stage, the original Ethernet
II frame is converted to an Ethernet SNAP frame and then finally to an
IEEE 802.10 frame. This conversion is required to maintain compatability
and reliability between the two different topologies. The most
important bit to remember here is the SAID field and its purpose.
Summary
This page introduced four popular VLAN
tagging methods, providing you with the frame structure and general
details of each tagging method. Out of all, the IEEE 802.1q and ISL
tagging methods are the most popular, so make sure you understand them
quite well.

No comments:
Post a Comment